USE CASES
Reduce risk, accelerate hunting and investigation, and consolidate existing toolsets with Corelight's complete range of on-prem, cloud, and SaaS-based solutions.
Threat hunting
Replace a standalone IDS with Corelight’s Open NDR Platform
Replace a standalone IDS with Corelight's Open NDR Platform, which delivers IDS alerts integrated with the evidence needed to investigate them.
Fingerprint encrypted connections
Fingerprint SSL or SSH connections via the JA3/HASH packages so analysts can identify and track attacker movements across encrypted channels.
Assess the scope of a malware attack
Pivot off a malware hash in Corelight’s files.log to immediately see all hosts that have downloaded the malicious file and then prioritize additional response work such as agent deployment.
Locate PCAP files needed for an investigation
Pivot from the logs of a Zeek®-parsed connection directly into connection packets in Moloch using the shared Community ID appended to the Zeek conn.log.
Verify containment and remediation
Use Zeek's network logs for conducting post-breach monitoring to look for the recurrence of malware beaconing.
Improve defensibility
Use Zeek's continuous logging across protocols to establish the "ground truth" of what happened historically, minimizing both legal expenses and the scope of disclosure.
Get insights into SSH connections without decryption
Investigate a suspicious SSH connection and see evidence of file transfers and human keystroke activity via insights from Corelight’s Encrypted Traffic Collection.
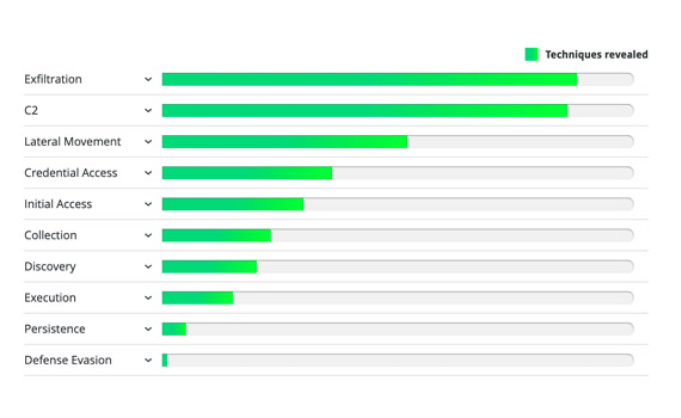
Find ATT&CKs with Corelight
Corelight's alerts and network evidence help you uncover a wide range of adversary tactics, techniques, and procedures (TTPs) within the MITRE ATT&CK® framework.
Incident response
Get insights into SSH connections without decryption
Investigate a suspicious SSH connection and see evidence of file transfers and human keystroke activity via insights from Corelight’s Encrypted Traffic Collection.
Assess the scope of a malware attack
Pivot off a malware hash in Corelight’s files.log to immediately see all hosts that have downloaded the malicious file and then prioritize additional response work such as agent deployment.
Threat detection
Detect lateral movement
Detect lateral movement in MITRE ATT&CK related to SMB and DCE-RPC traffic, such as indicators targeting Windows Admin Shares and Remote File Copy. Stream Zeek logs to the Real Intelligence Threat Analytics (RITA) tool to create a daily report of potential beaconing activity.

Fingerprint connections for fraud detection
Create custom Zeek logs to fingerprint connections and identify issues like API fraud and account takeovers.
Data enrichment
Identify vulnerable software
Use Zeek’s software.log to identify outdated or vulnerable software, such as Java or Flash, running in an environment.
Flag Cyrillic keyboard usage
Monitor Zeek’s rdp.log to identify the use of Russian character set keyboards in an environment, which could signal unusual behavior.
Fingerprint connections for fraud detection
Create custom Zeek logs to fingerprint connections and identify issues like API fraud and account takeovers.
Network operations
Create inventories of connected devices
Inventory network-connected devices and their services without needing to install host agents, and use Zeek’s software.log to monitor BYO software used by employees.
Troubleshoot a load balancer issue
Diagnose a load balancer performance problem that is difficult or impossible to replicate in a lab environment via evidence gathered from Zeek’s network logs and end finger pointing between security and network operations teams.





























